Secure applications using Dynamic RPC Ports
Securing your Windows Server running applications using Dynamic RPC Ports can be a little frustrating but it doesn’t have to be. RPC stands for Remote Procedure Call and it is basically used to establish communication between client/server applications. We aren’t going to go into detail about what RPC is or does but we are going to tell you how to best secure your Windows Server firewall that is hosting applications that use Dynamic RPC ports.
Follow the steps below if you ever find yourself having to secure applications using Dynamic RPC Ports on a Windows Server whether it’s Windows Server 2008 or Windows Server 2012.
Step 1 – Open Firewall log
On the Windows Server, open the firewall log in order to see what packets are being dropped.
Step 2 – Open TCPView
On the Windows Server, open TCPView from the Sysinternals Suite. This utility will display every TCP connection on the server along with the program and port of each connection.
Step 3 – Analyze firewall log
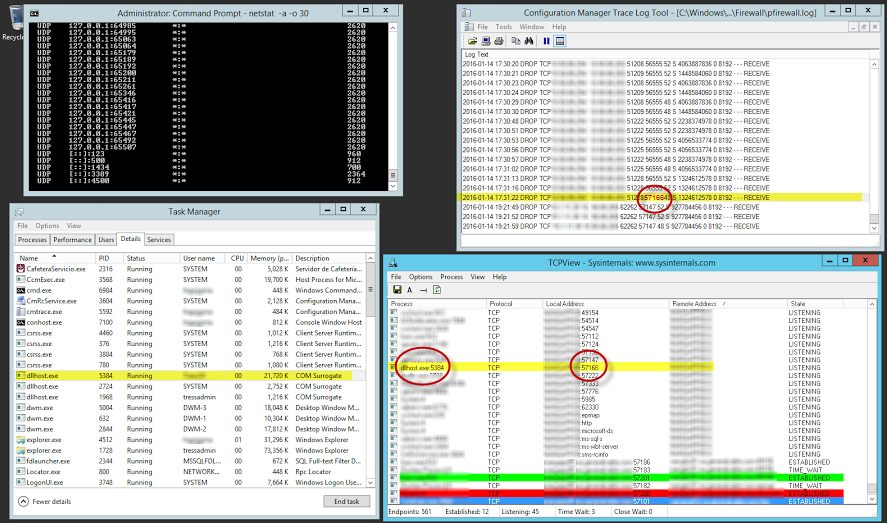
Notice the TCP port of 57166 being dropped in the firewall log located on the Windows Server in %windir%\system32\logfiles\firewall\pfirewall.log. Make a note of the port (57166 in this example).
Step 4 – Analyze TCPView
Now look for that port in TCPView. Once you find it, look at the program using it. In our example the program is dllhost.exe.
Step 5 – Create Firewall Inbound Rule
Open up the Firewall on the Windows Server and create a new Custom Inbound Rule.
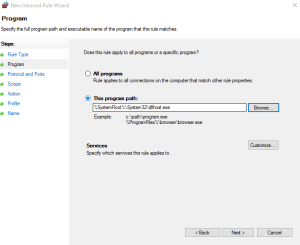
Type in the full path of the program from Step 4
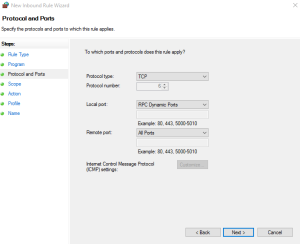
Select TCP as the Protocols type and RPC Dynamic Ports for the Local Port
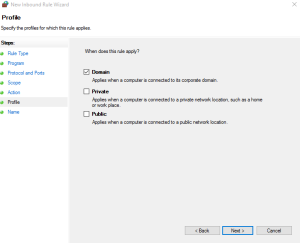
Select the default values for the next couple of sections of the Firewall Rule Wizard and make sure to apply this rule to your Domain Profile
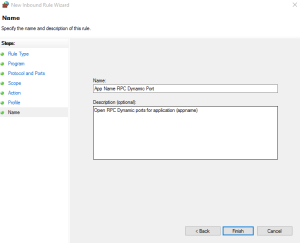
Finally, give the Inbound Rule a meaningful name and description
References
https://support.microsoft.com/en-us/kb/929851
http://www.liutilities.com/products/wintaskspro/processlibrary/dllhost/
https://technet.microsoft.com/en-us/library/cc732839(v=ws.10).aspx