Restrict remote desktop users to a single session
You can restrict remote desktop users to a single session on a Windows RDS or Terminal server. This is the default behavior out of the box. However, I’ve seen instances where it can cause some weird behavior if this policy is not explicitly enabled. For example, if a user doesn’t close his or her sessions by logging off but instead hits the “X” in the upper right corner to close their remote desktop session. By default, this leaves their session in a disconnected state on the terminal server. When the user attempts to reconnect, it will automatically reconnect to that session on the Remote Desktop Host Server.
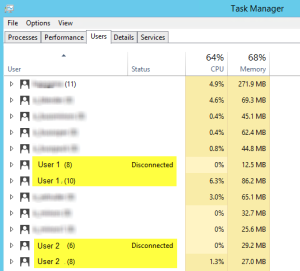
However, I’ve seen some quirky behavior where a user reconnects but is presented a “black” screen. When you view the logged on sessions on the RDS server, you’ll notice two sessions for the user. By the way, to view your RDS users on a Windows 2012 R2 RDS server, use the Task Manager and then select the Users tab. Notice how there is one user account in a disconnected state while the other is in an “Active” state. The status doesn’t actually state “Active, but a “blank” status means it is active. Hmm…not what I was expecting.
To be honest, I have only witnessed this behavior on a Windows 2012 R2 Remote Desktop Services server. I haven’t seen this happen on a Windows 2008 R2 RDS server. To resolve this, just follow the steps below.
- Logon to server “RDS/Term Server”
- Run GPEDIT.MSC
- Navigate to the following path:
Computer Configuration\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Connections\
- Enable the following policy
“Restrict Remote Desktop Services users to a single Remote Desktop Services session“
Instead of editing the local policy on your terminal server, you can, of course, create a Group Policy object and apply it to your terminal servers if you wish.
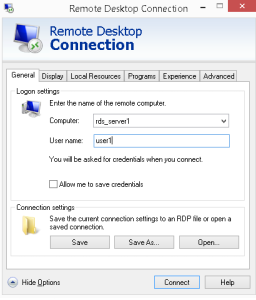
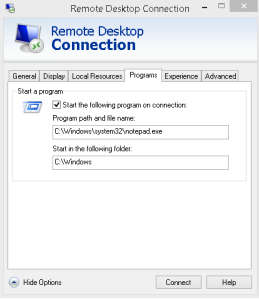
One other note I’d like to mention is that even though you force ENABLE the “Restrict Remote Desktop Services users to a single Remote Desktop Services session” policy, there is a scenario where this doesn’t restrict a user account to a single session. If a user configures a RD connection to the desktop of the terminal server which is common. That user will receive a Desktop on the terminal server. If that same user creates another RD connection (using mstsc.exe for example) but this time, instead of creating a RD connection to a desktop on the terminal server, they configure the Program tab to open a specific program to open automatically when they connect to the terminal server (we used to call that Kiosk mode), that user will be allowed to log on with a second active session which is completely separate from the first session. Therefore, that user can have multiple sessions to a terminal server even though the Restrict RDS policy is enabled.
I’m not sure whether this is intentional or not and whether or not it even matters but I thought this was interesting behavior. If anyone knows whether this is by design or has any further details about this, please feel free to comment or drop me an email via the contact form. Thank you!